DoS and DDoS attack in cyber security
In the vast landscape of cybersecurity threats, DoS and DDos attacks loom large, showcasing their disruptive potential. These attacks employ a network of infected systems, orchestrated by cybercriminals to flood a targeted resource. The result? A denial of service to legitimate users trying to access that resource.
The Menace of DDoS Attacks
DDoS attacks emerge as formidable weapons in the cyber arsenal due to their sheer power. A website’s sudden unavailability often signifies it has succumbed to such an assault. Hackers, by inundating the website or PC with overwhelming traffic, effectively crash the system, causing an overload beyond its capacity.
Historical Instances: A Glimpse Into the Impact of DoS and DDos
The infamous case involving Michael Calce, known online as “Mafiaboy,” epitomizes the disruptive potential of DDoS attacks. In 2000, at the age of 15, Calce orchestrated one of the initial DDoS attacks. Exploiting various university computer networks, he launched an assault that brought down prominent websites like eBay and Yahoo.
In 2016, Dyn encountered a colossal DDoS attack, impacting major online platforms and services, including Netflix, PayPal, Amazon, and GitHub.
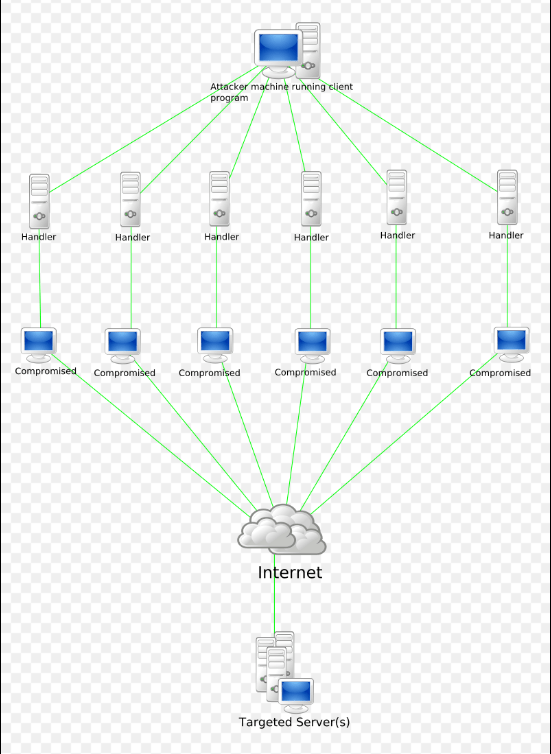
Understanding DoS and DDoS
DoS Attack Overview
Denial of Service (DoS) represents an attack targeting a service to disrupt its normal operations, rendering it inaccessible to users. Typically, this attack focuses on online services such as websites but can extend to networks, machines, or specific programs.
Key Differences: DoS and DDoS
Differentiating between DoS and DDoS attacks elucidates their operational dissimilarities:
- DoS: Operates via a single system targeting the victim system.
- DDoS: Engages multiple systems attacking the victim’s system simultaneously.
- Speed: DoS is slower compared to the swift pace of DDoS attacks.
- Blocking Difficulty: DoS attacks are relatively easier to block due to their single-system nature, whereas DDoS attacks pose challenges as they originate from multiple devices.
Variants of DDoS Attacks
1. Volumetric Attacks
These prevalent DDoS assaults leverage botnets to inundate networks or servers with excessive traffic, overwhelming their processing capabilities. Consequently, network bandwidth is compromised, potentially resulting in a complete denial of service.
2. Protocol Attacks
Exploiting vulnerabilities in the TCP connection sequence, these attacks manipulate the three-way handshake, leaving targeted ports unavailable to process further requests, effectively shutting down servers.
3. Application Attacks
These stealthier attacks, targeting the victim’s applications at a slower pace, mimic legitimate user requests, rendering the victim unable to respond. They pose a significant challenge for companies in detection due to their nuanced approach.
4. Fragmentation Attacks
Exploiting weaknesses in the datagram fragmentation process, these attacks render fake data packets impossible to reassemble, leading to disruption.

Unraveling DDoS Attack Methodologies
DDoS attacks exhibit simplicity in their logic but vast diversity in execution. These attacks focus on specific layers within network connections, such as:
- Layer-3 (Network Layer): Engages attacks like Smurf Attacks, ICMP Floods, and IP/ICMP Fragmentation.
- Layer-4 (Transport Layer): Includes SYN Floods, UDP Floods, and TCP Connection Exhaustion.
- Layer-7 (Application Layer): Targeting HTTP-encrypted attacks.
Safeguarding Against DDoS Attacks
- Prompt Identification: Swift detection of DDoS attacks is pivotal to mitigating their impact. Employ technologies that enable rapid recognition and response to heavy traffic influxes.
- Firewall and Router Configuration: Configure firewalls and routers to reject spurious traffic while ensuring they’re updated with the latest security patches for enhanced protection.
- Leveraging Artificial Intelligence: Incorporate AI-driven systems to fortify existing defenses, offering proactive defense mechanisms against evolving attack methodologies.
- Securing IoT Devices: Employ trusted security software and ensure regular updates to prevent IoT devices from being compromised and potentially becoming part of a botnet.
Top DDoS protection websites and companies below
- Cloudflare: Renowned for its content delivery network (CDN) services, Cloudflare also offers comprehensive DDoS protection. It provides advanced security features to mitigate and prevent various types of DDoS attacks, ensuring uninterrupted access to websites and web applications.
- Akamai: Another prominent player in the cybersecurity landscape, Akamai, delivers DDoS mitigation services that focus on network security and protection against volumetric, application-layer, and other sophisticated attacks. It leverages a global network infrastructure to absorb and mitigate large-scale DDoS attacks effectively.
- Imperva Incapsula: Specializing in cloud-based security solutions, Imperva Incapsula provides DDoS protection services designed to safeguard websites and applications against various attack vectors. It offers real-time monitoring, automated mitigation,
Also read related article
FAQs: Insights DoS and DDoS
- What Constitutes a DoS Attack? A DoS attack aims to render a machine or network inaccessible by flooding it with excessive traffic or triggering crashes through information bombardment.
- What Defines a DDoS Attack? DDoS attacks endeavor to incapacitate a particular service by directing continuous, substantial traffic from multiple systems.
- Enumerating Different DoS Attacks:
- Buffer overflow attacks
- Ping of Death or ICMP flood
- Teardrop Attack
- Flooding Attack




1 comment