Understanding SIEM: Security Information and Event Management
cybersecurity remains a critical concern for businesses worldwide. The increasing methods cyber threats demands robust, proactive measures to safeguard sensitive data and infrastructure. Among the solutions of cybersecurity tools available, Security Information and Event Management (SIEM) solutions stand out as an indispensable asset.
What is Security Information and Event Management (SIEM)?
Security Information and Event Management (SIEM) represents a cybersecurity solution designed to identify, analyze, and mitigate security threats within an organization’s infrastructure. It achieves this by collecting and correlating real-time and historical data from diverse sources. These sources often include firewalls, Intrusion Detection Systems (IDSs), and various network devices.
Key functions of Security Information and Event Management (SIEM) Solution
- Centralized Data Storage: SIEM solutions act as centralized repositories, adeptly collecting logs, events, and other security-related data from multiple sources. This consolidation streamlines the monitoring and analysis processes.
- Event Correlation and Threat Detection: An important aspect of SIEM involves contextualizing and correlating seemingly disparate security data. By identifying complex attack patterns and potential breaches, SIEM enables proactive threat detection and response.
- Incident Response Automation: One of the features of SIEM is its ability to automate incident response. Upon detecting potential threats, SIEM solutions facilitate timely mitigation, thereby enhancing an organization’s cybersecurity posture.
- Intuitive Reporting Dashboards: Most SIEM solutions offer user-friendly dashboards that visually represent security data and insights. These dashboards empower organizations to comprehend their security status and identify areas necessitating improvement.
Shift from Traditional vs Modern Security Information and Event Management (SIEM)
Traditionally, SIEM solutions had limitations in detecting dynamic threats, relying primarily on static analysis based on predefined metrics and triggers. However, modern SIEM solutions have revolutionized cybersecurity by integrating artificial intelligence (AI). This AI augmentation allows for in-depth analysis of user behavior, significantly enhancing the detection of advanced, dynamic attacks that exclude traditional methods. For instance, an AI-powered SIEM solution can swiftly flag a user exhibiting unusual activity, such as sudden access to sensitive files or unauthorized attempts to manipulate data. Subsequently, it can alert administrators or autonomously take measures like restricting access, thereby thwarting potential security breaches
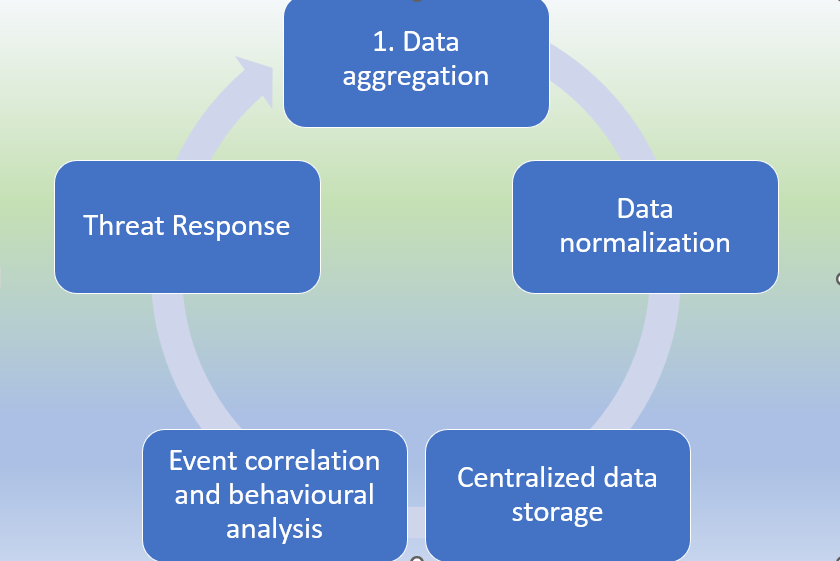
Generic Security Information and Event Management SIEM Workflow below
- Data Aggregation: SIEM tools aggregate data from multifarious sources, ensuring a comprehensive scope for analysis.
- Normalization: Normalization of collected data into a standardized format is pivotal for effective correlation and contextualization.
- Centralized Storage: Data is stored in a centralized repository, facilitating streamlined access and analysis.
- Event Correlation: SIEM employs event correlation, drawing insights from historical and real-time data to detect potential threats.
- Machine Learning Integration: Leveraging machine learning, SIEM establishes baselines of normal user behavior, swiftly flagging deviations as potential security threats.
- Incident Response: Upon threat detection, SIEM can autonomously respond or provide crucial context and data to security teams for prompt intervention.
SIEM vs CSPM Distinguishing Features
While both SIEM and Cloud Security Posture Management (CSPM) are important in preventing cybersecurity, their roles differ significantly.
- SIEM Focus: SIEM concentrates on aggregating and analyzing security events across diverse IT infrastructures.
- CSPM Role: In contrast, CSPM specializes in scanning cloud infrastructures, identifying security gaps, misconfigurations, and vulnerabilities within cloud environments.
SIEM vs. CIEM: A Comparative Analysis
Distinguishing between SIEM and Cloud Infrastructure Entitlement Management (CIEM) sheds light on their distinct scopes and functionalities.
- SIEM Focus: SIEM specializes in collecting and analyzing data from varied sources to detect and prevent security threats.
- CIEM Role: On the other hand, CIEM primarily manages cloud entitlements, scanning cloud environments for vulnerabilities and offering insights into resource utilization.
The Benefits of Deploying Security Information and Event Management (SIEM) Solutions
- Threat Mitigation: SIEM’s robust analysis of real-time and historical data prevents malicious actors from compromising critical data and applications.
- Swift Incident Response: In the event of a security breach, SIEM facilitates rapid response, minimizing potential damage and data loss.
- Regulatory Compliance: SIEM aids in achieving compliance with regulatory frameworks like HIPAA or PCI DSS, enhancing overall security protocols.
- Insider Threat Prevention: Leveraging advanced behavioral analytics, SIEM effectively detects and prevents insider threats.
- Enhanced Security Strategies: Through data-derived insights, SIEM empowers security teams to craft robust policies and enforce stringent controls.
Also read related article on security
See one of best videos on YouTube related to SIEM



3 comments